Protecting your AWS account access keys is critical for protecting your company's cloud infrastructure. Managing several accounts, on the other hand, can be complicated and time-consuming. aws-vault secures the storage and management of access keys for many AWS accounts.
What is AWS-Vault?
AWS Vault is a tool to securely store and access AWS credentials in a development environment.
AWS Vault stores IAM credentials in your operating system's secure keystore and then generates temporary credentials from those to expose to your shell and applications. It's designed to be complementary to the AWS CLI tools and is aware of your profiles and configuration in ~/.aws/config.
The AWS-vault program generates temporary credentials using Amazon's STS service via the GetSessionToken or AssumeRole API calls. Because these temporary credentials expire in a short period, the risk of credentials leaking is decreased.
The Problem
The ~/.aws/credentials file is typically located in the home directory of a user on a Unix-like system (such as Linux or macOS) or at C:\Users\USERNAME\.aws\credentials on Windows and is used by the AWS Command Line Interface (CLI). The file contains sensitive information, including AWS access keys and secret access keys, which provide access to your AWS resources. Personally, for me, I have never been the biggest supporter of ~/.aws/credentials because of its vulnerability to potentially malicious actors.
Solution
Install AWS-Vault
By downloading the latest release
on Windows with Chocolatey:
choco install aws-vaulton macOS with Homebrew Cask:
brew install --cask aws-vaulton Linux with Homebrew on Linux:
brew install aws-vault
AWS-Vault Backend
The backends in which credentials are stored include:
Secret Service (Gnome Keyring, KWallet)
Encrypted file
NB - Gnome Keyring and KWallet can be used on Windows when using WSL.
Configure AWS-Vault
Add AWS region in ~/.aws/config before adding a profile.
[default]
region = us-east-1
Add AWS-Vault profile
# Store AWS credentials for the "jonsmith" profile
$ aws-vault add jonsmith
Enter Access Key Id: ABDCDEFDASDASF
Enter Secret Key: %%%
# Execute a command (using temporary credentials)
$ aws-vault exec jonsmith -- aws s3 ls
bucket_1
bucket_2
# open a browser window and login to the AWS Console
$ aws-vault login jonsmith
# List credentials
$ aws-vault list
Profile Credentials Sessions
======= =========== ========
jonsmith jonsmith sts.GetSessionToken:46m29s
# Start a subshell with temporary credentials
$ aws-vault exec jonsmith
Starting subshell /bin/zsh, use `exit` to exit the subshell
$ aws s3 ls
bucket_1
bucket_2
AWS-Vault with Roles and MFA
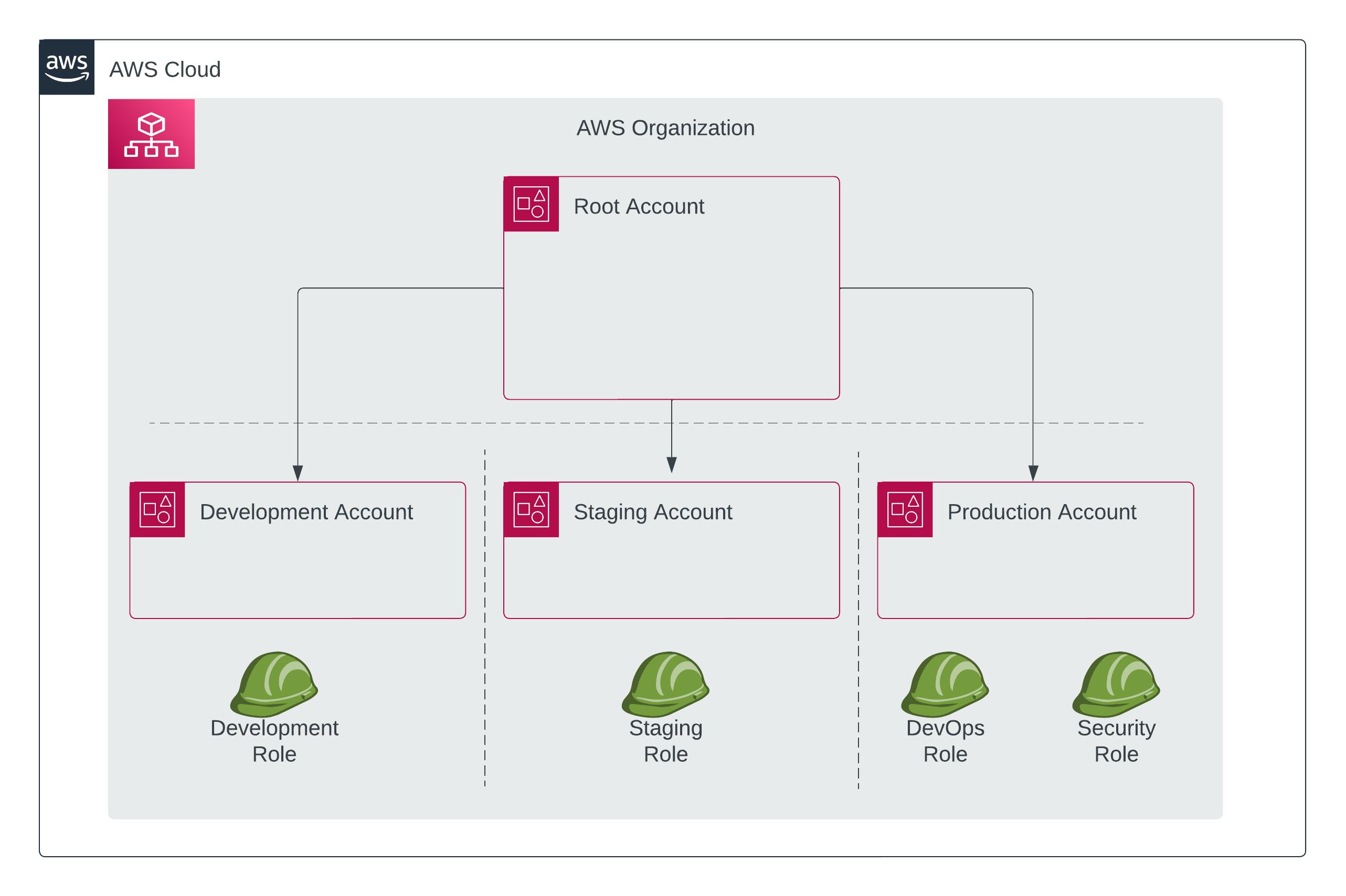
Using roles and multi-factor authentication (MFA) are important best practices when working with AWS to enhance security. As such you would need to create an IAM User and Roles in addition to setting up a MFA device whether virtual or physical.
The diagram below depicts a typical setup of AWS Organization.
[default]
region = us-east-1
[profile jonsmith]
mfa_serial = arn:aws:iam::111111111111:mfa/jonsmith
region = us-east-1
[profile Development-Role]
source_profile = jonsmith
region = us-east-1
role_arn = arn:aws:iam::22222222222:role/Development
mfa_serial = arn:aws:iam::111111111111:mfa/jonsmith
[profile Staging-Role]
source_profile = jonsmith
region = us-east-1
role_arn = arn:aws:iam::22222222222:role/Staging
mfa_serial = arn:aws:iam::111111111111:mfa/jonsmith
[profile DevOps-Role]
source_profile = jonsmith
region = us-east-1
role_arn = arn:aws:iam::333333333333:role/DevOps
mfa_serial = arn:aws:iam::111111111111:mfa/jonsmith
[profile Security-Role]
source_profile = jonsmith
region = us-east-1
role_arn = arn:aws:iam::333333333333:role/Security
mfa_serial = arn:aws:iam::111111111111:mfa/jonsmith
Refer to the AWS-Vault official repo for additional info:

